CCPA and Your IT Plan for Data Security
by Elaine Evans, on Jan 14, 2020 4:57:40 PM

You may have heard of the California Consumer Privacy Act and know that it is bringing more stringent data protection laws than we’ve seen yet. And, while its name leads you to believe that it is purely for businesses in California, the truth is that it has a much wider impact. If you gather personal data within California or do any businesses within California, then you are potentially subject to CCPA.
Much of the information out there is about building and tracking compliance around the right to know, access, opt-out, etc for organizations dealing with that pickle. However, did you also know that there are data security requirements as well?
CCPA requires “reasonable" security, which can be interpreted in many ways (the link refers to a 2016 California Data Security Breach Report where the term is used). Still, there are some basic items that everyone should have in place. For instance, if your organization cannot even centrally enforce that a Mac is password protected, then you have a problem.
The headline is that if you have nothing in place, then you are putting your business, your clients and the consumer at risk and can be held accountable under these ever-growing data protection laws.
What are reasonable security measures?
Now more than ever, our people are accessing data on multiple devices through integrated services. So, how do you assure that you have taken “reasonable” security measures?
First, answer this simple, ten-question survey to see where you stand:
- Are you able to be remotely wiped/locked through a central administrative console if lost/stolen/compromised?
- Do you have a way to make sure software is updated/patched on your devices?
- Can you centrally enforce a password policy?
- Can you centrally enforce device encryption?
- Do you have endpoint protection running to detect/remediate threats?
- Do you have a BYOD (“bring your own device”) policy for your people accessing company information on personal devices?
- Do you have the ability to cut all accounts/services for people on non-company owned devices?
- Do you have multi-factor authentication set up for your services to prevent unauthorized logins after a login has been compromised?
- Do you have a way to prevent your people from emailing/sharing protected data?
- Do you have any phishing scam awareness training?
If you checked off less than five of these, then you need to think seriously about your IT strategy.
Securing Devices, People, and Services
"Data Security" is a broad term in an organization, so I usually break it down to make sure people are thinking of three main tracks: your devices that have access to company data, your people, and the services they use that have access to company data. These are usually interconnected, but it helps to look at them separately to make sure you are crafting a complete plan.
| What devices are accessing company data or the network that is linked to company data? Think about computers, mobile devices, your wireless appliances, printers and more. |
- If the devices live in the office and stay there, you can usually put some best practices in place to secure your network that will limit your risk
- If the devices leave the office network, you will want to put something in place like an MDM to make sure they have data security best practices enforced
- Make sure to use endpoint protection software for all of your devices (yes, even Macs need anti-virus running)
|
How are people accessing data in your organization? Think about the potential for human error such as walking away from logged in devices, sharing password credentials, and more. |
- Plan your defined security permissions based on role
- Require individuals to use unique logins to access company data always
- Teach about security best practices like how to spot a phishing scam or not to have their password the same for every account
| What services contain or have access to company data? Think about SaaS/software products, cloud tools like AWS or Azure and other third party services. |
- Look into documentation on their security measures for their product
- Leverage features like data loss/leakage prevention to keep your team from doing things like emailing social security numbers or other PI
- Make sure secure connections are in place and leverage multi-factor authentication whenever possible
There are a lot more items to consider, but beginning to look at your data security in these terms will put you on the path to being aligned with existing and coming data security measures.
Use Experts
There are many ways to approach data security. When push comes to shove, you should always consult a data security expert who has experience in consulting on any compliance that applies to your organization. You should also rely on IT experts to help enact the plan that your Data Security Expert recommends. Similar to building a house when you have an inspector and a contractor, data security has people who judge if you are compliant and people help to get you there. Think of it this way -- a Data Security Expert will tell you that you need a closet for a room to be considered a bedroom, but the IT Expert will help you pick the best layout and build the closet for you.
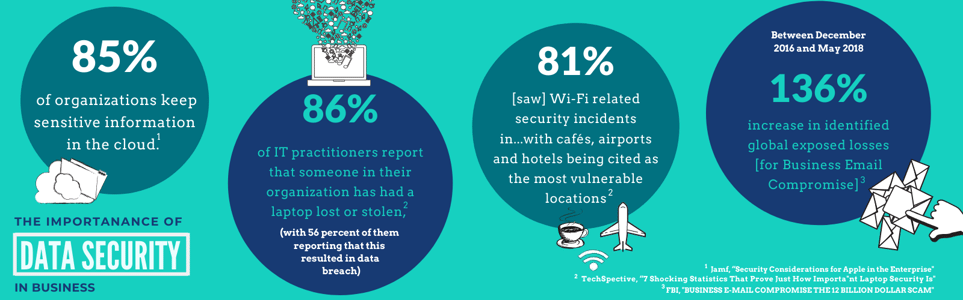
Shocking Stats
Think it won’t happen to you or willing to risk it to save the money now? Many companies do this, but many do it without really understanding exactly what they are risking. Below are some stats to show the reach and impact of data security breaches.
We can help
If you don't know where to start, please reach out to us and we're happy to help you start to put best practices in place for your IT strategy. Springboard IT has helped hundreds of businesses put best practices in place that protect company data . We’re Apple IT experts that understand businesses need someone they can trust to help navigate these business critical concerns.
Springboard IT is part of the Apple Consultants Network. We have a core competency of Apple IT and how to build an entire business using Apple IT or how to integrate Apple into your company’s larger IT ecosystem. Therefore, our blogs usually focus with this Apple IT centric assumption, but have parts that will carry across any platform.
CREDITS
Icon made by kiranshastry from www.flaticon.com
Icon made by Freepik from www.flaticon.com
Photo by Liam Tucker on Unsplash