It seems that we can't go a week without hearing about some new security breach involving tens of thousands or even millions of passwords, which is even more worrisome with the recent Netflix email scam.
That’s why it’s essential that you use strong passwords comprised of random characters and manage them in a full-featured password manager like 1Password or LastPass. For a more straightforward approach, there's iCloud Keychain, which is the password management system developed by Apple available on every macOS and iOS device. Beyond using a password management system, many large companies like Apple, Google, Facebook, and Dropbox offer an option for a higher level of security, called two-step verification.

What is two-step verification?
Two-step verification is an authentication method in which a computer user is granted access only after successfully presenting two (or more) pieces of evidence proving their ownership of account. For example, it's similar to providing two different forms of identification when flying internationally or closing on a home. Without this double verification someone looking to commit fraud only needs your one password, or one form of ID, to wreak havoc.
An account that’s protected by two-step verification requires the user to enter a temporary key, typically sent to your phone via text, call, or email. These temporary secondary passwords are only valid for a short period time and can be used only once, to ensure security and anonymity. Conveniently, you only have to enter these secondary passwords the first time you log-in on a particular device or web browser, adding an occasional extra step, not a daily inconvenience.
How does two-step verification work?
Sites that offer two-step verification will provide setup and usage instructions, but the basics are as follows. You’ll enable two-step verification in the account settings, and then tell the site how you want to receive the one-time password, generally by providing your phone number or email.
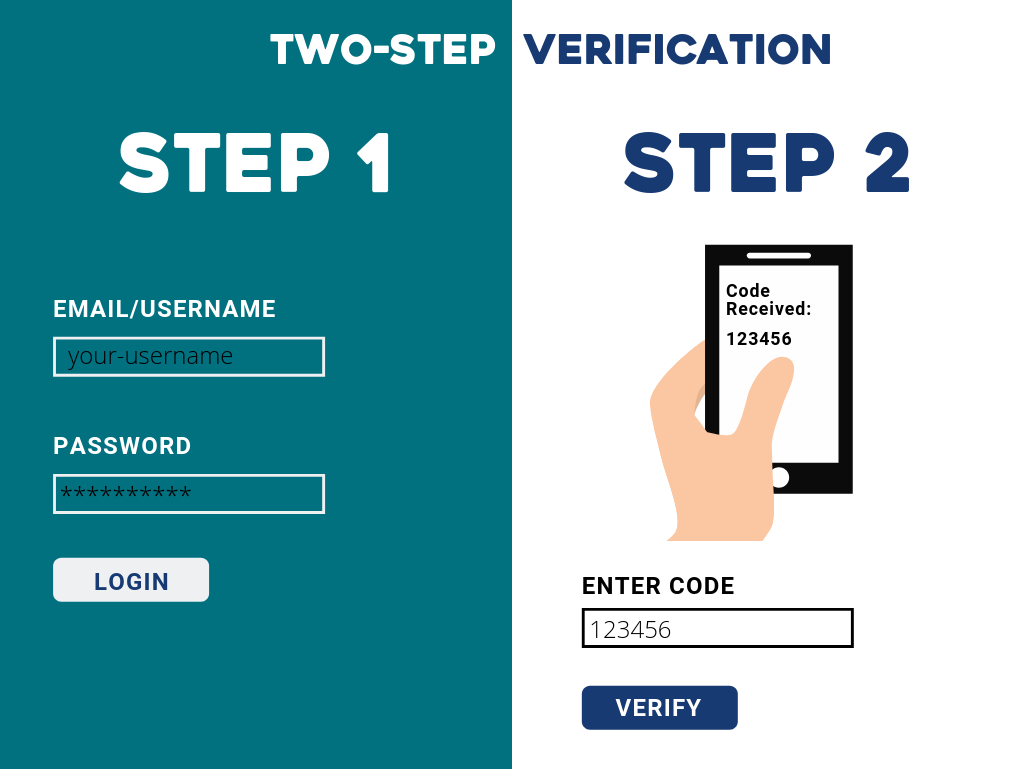 When it comes time to log into a service protected by two-step verification, you’ll enter your username and password as usual. After that, you’ll be prompted to receive a one-time password and the service will send it to you via text, email, or phone call. You'll be given a period of time (usually 5 or 10 minutes) to enter the temporary code before it expires. This dual layer of protection makes breaking into your account much more challenging to a potential hacker.
When it comes time to log into a service protected by two-step verification, you’ll enter your username and password as usual. After that, you’ll be prompted to receive a one-time password and the service will send it to you via text, email, or phone call. You'll be given a period of time (usually 5 or 10 minutes) to enter the temporary code before it expires. This dual layer of protection makes breaking into your account much more challenging to a potential hacker.
When do I need two-step verification?
Most sites that use two-step verification don’t require that you enter a one-time password on every login, since that would be overkill. For important accounts—email, social media, cloud services, banking—you absolutely should use two-step verification or fingerprint log-in for added protection so a bad guy can’t impersonate you to your friends, receive email-based password resets for other sites, or access your most important data. Large service providers, like Google offer very helpful resources and instructions for setting up this verification.
What's the difference between two-step verification and two-factor authentication?
You may also hear the term two-factor authentication, which is even more secure than two-step verification when implemented correctly. That’s because two-factor authentication combines something you know (your password) with something you have (such as a secure token key-fob that generates time-sensitive one-time passwords) or something that’s true of you (biometric info like a fingerprint or iris scan). It might seem like using your iPhone to get a text message or run an authenticator app qualifies, but if you end up doing everything on a single device that could be compromised, it’s not true two-factor authentication.
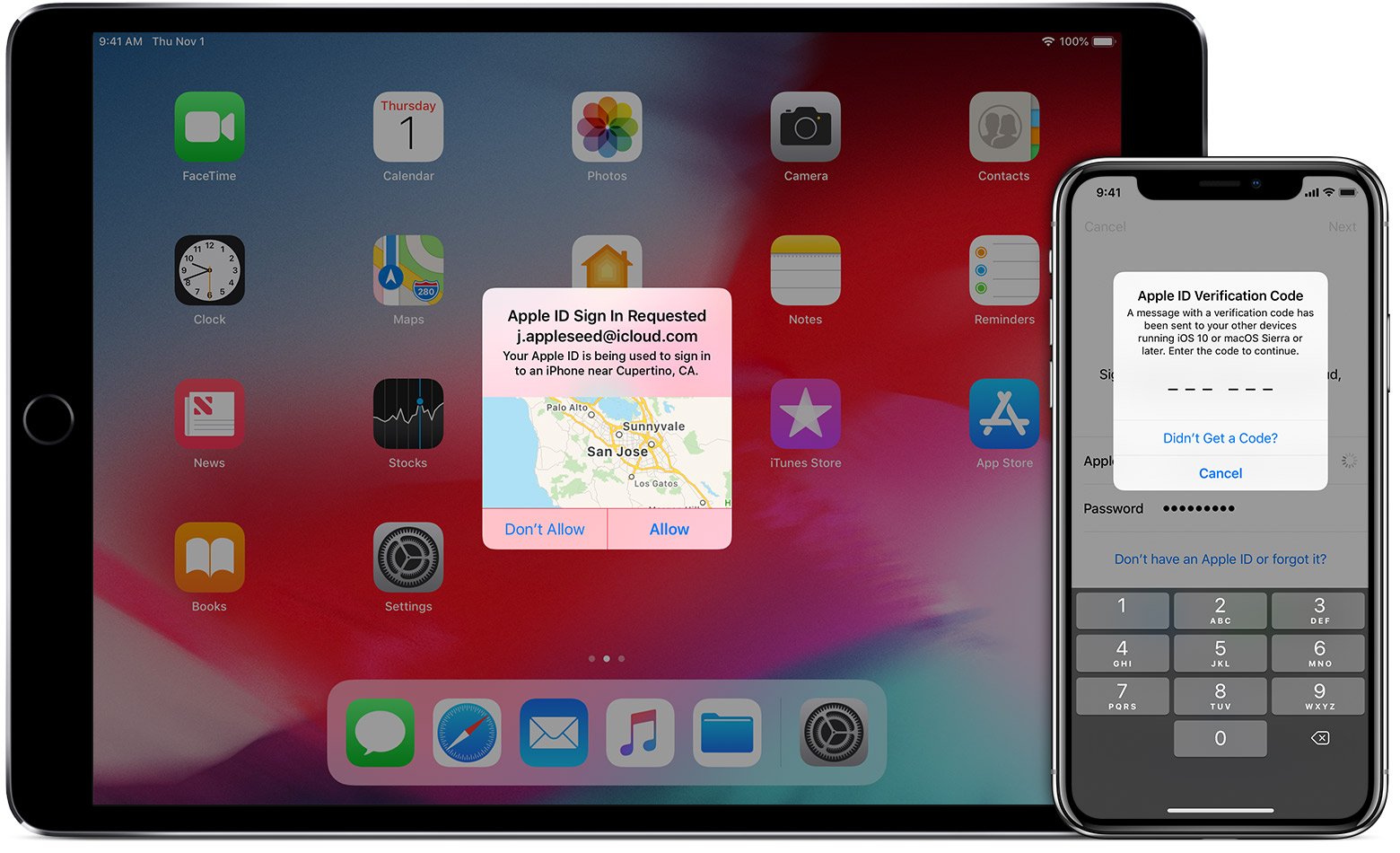 Regardless of the terminology, going beyond a single password, no matter how strong, significantly increases your security, and you would be well served to employ such a security technology for your most important accounts.
Regardless of the terminology, going beyond a single password, no matter how strong, significantly increases your security, and you would be well served to employ such a security technology for your most important accounts.
To learn more about best practices for keeping your accounts secure and for advice on how to protect your businesses precious data, contact of our business consultants for a FREE Apple Business Consultation.